UPDATE: There is a way to generate these certificates automatically. To find out how, read this post.
If you are writing a webhook server for Kubernetes Admission Controllers like ValidatingAdmissionWebhooks or MutatingAdmissionWebhooks, you must expose it over HTTPS. To run these servers on HTTPS, you need TLS certificates. There are solutions available which you can use to solve this problem, first and foremost that comes to my mind is cert-manager. It is a great project and automates this problem. But it is an added dependency that you might have to keep running in your cluster.
Self Signed Cert Generation
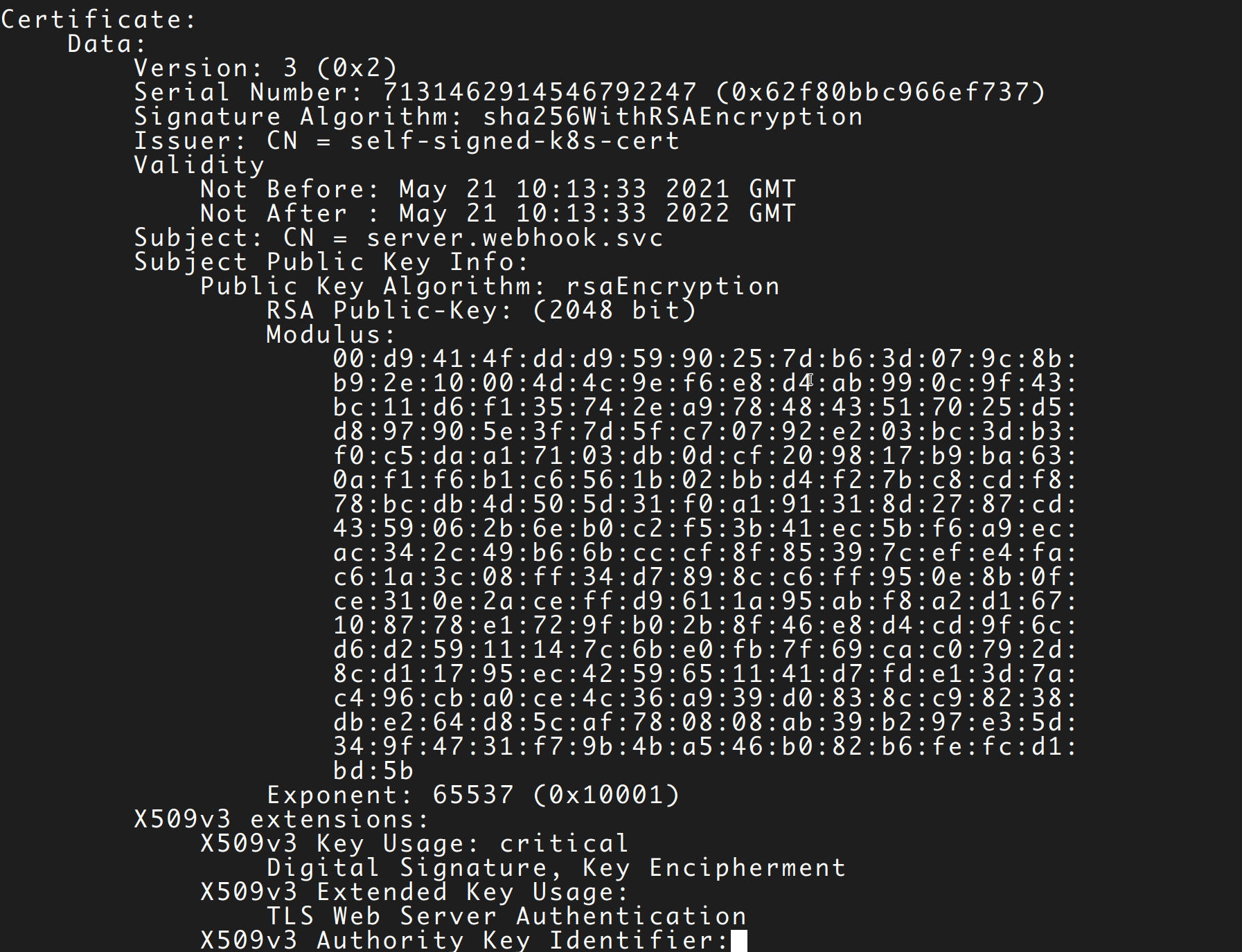
To avoid the added dependency of cert-manager and similar solutions, I chose to create a small tool to generate a certificate that you can use with your webhook server. The code for the tool is inspired by the Kubernetes test infra code. It takes in the service name and the namespace name and generates a private key and certificate in a temporary directory.
Install the tool by following these instructions. And once installed in your PATH, you can generate certificates by simply running the following command:
$ self-signed-cert --namespace=webhook --service-name=server
/tmp/self-signed-certificate311397173
And these three files generated in that directory:
$ ls /tmp/self-signed-certificate311397173
ca.crt server.crt server.key
Loading certs into the Helm chart
Now your webhook server helm chart can load those certs from the temporary directory. Helm has an excellent provision to do so. For example, you can simply add them to your values file with a flag like --set-file.
See the following flow of installation:
# Generate certs and store the path to certs in a variable.
certs=$(self-signed-cert --namespace validate-secrets --service-name validate-secrets)
# Now load those certs into the helm chart.
helm install mywebhookserver \
--set-file key=$certs/server.key \
--set-file cert=$certs/server.crt .
Note that the above certificates are not base64 encoded, so ensure that you encode them in your helm templates. Add a snippet that looks like the following:
key.pem: "{{ .Values.key | b64enc }}"
Loading certs for a Golang web server
Here I am showing how to load those certificates for serving into a webserver written in golang. For other programming languages, you can follow the required steps to expose a server with HTTPS support.
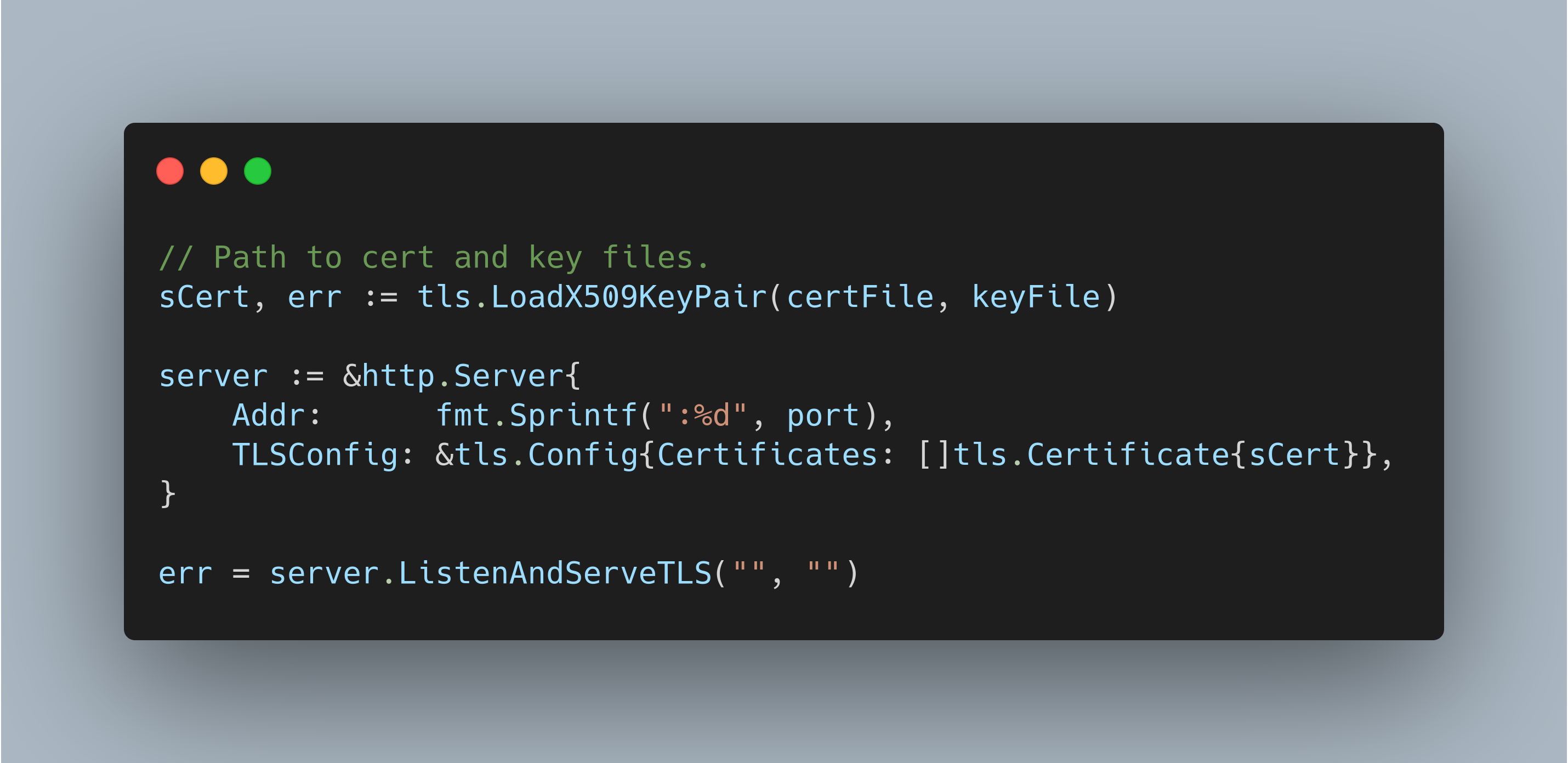
I have removed the error handling parts for simplicity of code, but please add them to your code.
Let me know what tools do you use to generate private certificates for the webhook servers.
UPDATE: There is a way to generate these certificates automatically. To find out how, read this post.